Web Skimmer Found Within EXIF Metadata – Threat Actor Uses Image Files to Exfiltrate Credit Cards
Malwarebytes Labs recently found credit card skimming code hidden with the metadata of an image file, a process known as ‘steganography.’ This image file would then be unknowingly loaded by compromised online stores and would allow the threat actor to launch client-side JavaScript and steal the credit card information from the target’s customers.
Utilizing a compromised WordPress plugin known as ‘WooCommerce,’ the offending code loads a favicon file from cddn[.]site/favicon/ico, a site that was triggered upon visiting the merchant’s website. This malicious favicon file is crafted to be the same favicon used by the compromised store as a logo for their brand. While on the surface, nothing seems out of the ordinary, and the loaded code seems to be a simple JavaScript code that loads a remote favicon file while also parsing some data as well.
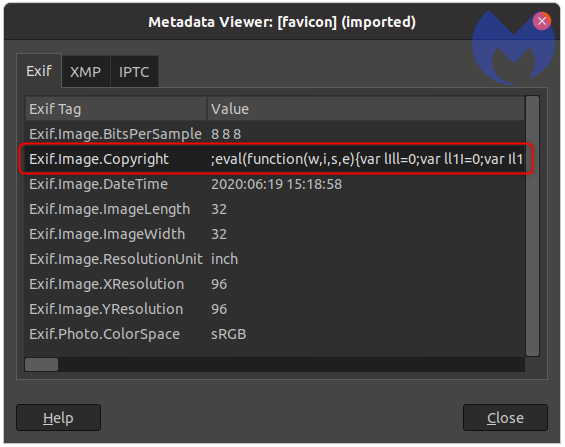
Using an EXIF viewer, Malwarebytes Labs was able to look deeper into the favicon’s metadata, specifically a field denoted as ‘Copyright.’ Within the Copyright field, the attackers were able to load their web skimmer, and through the EXIF viewer, Malwarebytes Labs were able to view the JavaScript code that was being injected. (see below) Malwarebytes Labs notes that while the abuse of image headers to hide malcious code is nothing new, this is the first time they witnessed it in conjunction with a credit card skimmer.
Initially, the malicious JavaScript loads the skimming portion of the code from the favicon.ico using an HTML image tag, <img>. As with other skimmers, this one also records the content of the input fields where online shoppers enter their name, billing address, and credit card information. What seperates this skimmer from others, though, is that while the stolen data is then encoded using Base64, the stolen data is then sent as an image file, via a POST request, to the threat actor. Malwarebytes Labs believes this image file technique is used to also conceal the exfiltrated data via the favicon.ico file.
Based on their analysis of the skimmer’s source code, having been found zipped and exposed in the open directory, is able to conclude that an earlier version of this skimmer was found hosted at jqueryanalise[.]xyz. While it lacks some of the obfuscation efforts found in the more recent version discussed earlier in the article, it has much of the same core features, such as loading JavaScript via the Copyright field in the image’s metadata. Malwarebytes Labs is also able to connect this threat actor to another skimming script based on the email used to register for the cddn[.].site (rotrnberg.s4715@gmail[.]com). Two domains (cxizi[.]net and yzxi[.]net) share the same skimmer code which looks much more elaborate and does not appear to have much in common with the other two JavaScript pieces.
Finally, this skimmer may have ties with Magecart Group 9. Security researcher @AffableKraut pointed out that a domain (magentorates[.]com) using this EXIF metadata skimming technique has the same Bulgarian host, same registrar, and was registered within a week of magerates[.]com. Magerates[.]com is registered under [email protected], which also has other skimmer domains, and in particular several used via another clever evasion technique in the form of WebSockets. This type of skimmer was tied to Magecart Group 9.
For Indicators of Compromise regarding this web skimmer, please see the attached PDF, ‘WebSkimmerIOCs.pdf.’
Sources:
